SSH Into IoT Devices: Remote Access Guide
Are you struggling to access your Internet of Things (IoT) devices when you're away from home or office? The ability to securely connect to and manage your IoT devices remotely is no longer a luxury, but a necessity in todays connected world.
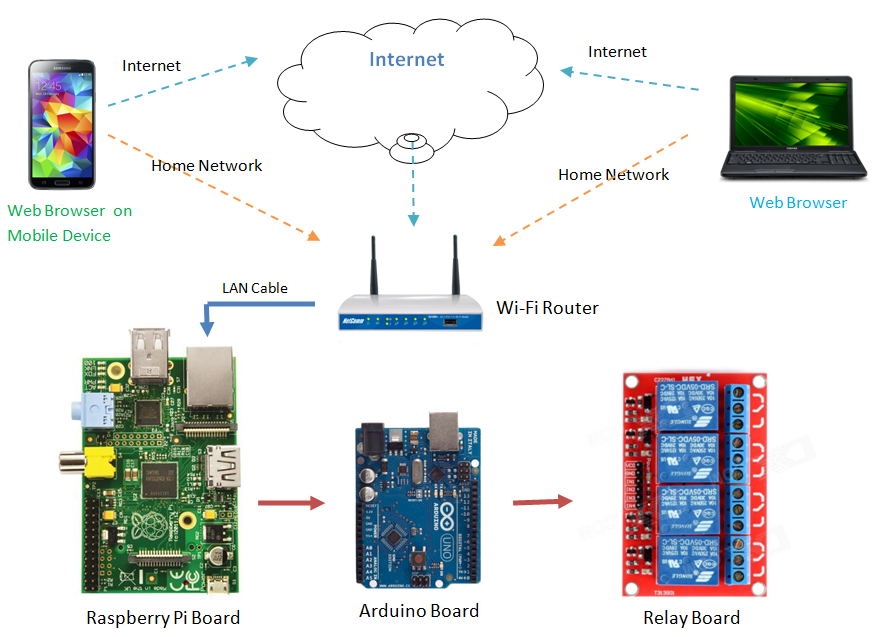
The landscape of the Internet of Things is rapidly evolving, bringing with it a plethora of devices designed to simplify our lives, automate processes, and gather valuable data. From smart home appliances to industrial sensors, these devices are generating a vast amount of information that can be used to improve efficiency, enhance security, and create new opportunities. However, the true potential of IoT can only be realized if we can effectively manage these devices, especially when they are located in remote locations or behind complex network setups.
This guide delves into the intricacies of establishing secure remote access to your IoT devices, ensuring that you can monitor, manage, and troubleshoot them from anywhere in the world. Whether youre a tech enthusiast, an IT professional, or simply someone looking to enhance their smart home setup, understanding how to configure remote SSH access is a critical skill. We'll explore the step-by-step process, encompassing everything from router configuration to device-specific settings, and address potential challenges along the way.
The Importance of Secure Remote Access
The core of successful IoT management revolves around the ability to remotely access and control your devices. This capability enables you to:
- Monitor Device Status: Keep tabs on the performance and operational status of your devices in real-time.
- Troubleshoot Issues: Quickly diagnose and resolve technical problems, minimizing downtime.
- Update Firmware: Maintain your devices with the latest security patches and feature enhancements.
- Configure Settings: Modify device parameters to adapt to changing needs or environments.
- Access Data: Retrieve the data collected by your devices for analysis and reporting.
However, remote access must always be approached with security in mind. Without proper safeguards, your devices and the data they generate can become vulnerable to cyberattacks. This is where the secure shell (SSH) protocol, combined with a robust network configuration, becomes paramount.
Unveiling the Essentials of Remote SSH for IoT Devices
The cornerstone of secure remote access lies in understanding the components involved and the steps necessary to establish a protected connection. These are some of the key steps needed:
- Movierulz Proxies Risks Legal Alternatives What You Need To Know
- Sammy Thighs Bio Tiktok Onlyfans More Latest Updates
- Enabling SSH on Your IoT Device: The foundation of remote access is ensuring that SSH service is active and properly configured on the IoT device itself.
- Finding Your Device's IP Address: Identifying the device's IP address within your local network or the public IP address of your router is essential for establishing a connection.
- Configuring Port Forwarding: This is a crucial step to "punch a hole" in your router's firewall, allowing incoming SSH connections to reach the IoT device.
- Using Dynamic DNS (DDNS): DDNS services are invaluable for keeping track of your router's changing public IP address, especially if your internet service provider (ISP) assigns dynamic IP addresses.
- Setting Up SSH Key Authentication: This adds an extra layer of security, using cryptographic keys to authenticate users, making it much harder for unauthorized individuals to gain access.
- Adding VPN Protection (Optional, but Recommended): Utilizing a virtual private network (VPN) creates an encrypted tunnel for all traffic, further securing your connection, especially over public or untrusted networks.
Let's take a closer look at these steps, providing practical advice to guide you through the process.
Step-by-Step Guide to Setting Up Remote SSH Access
1. Enabling SSH on Your IoT Device:
The first step is to enable SSH on your IoT device. This process varies depending on the operating system and the device itself.
- Linux Devices (e.g., Raspberry Pi, Arduino with Linux): Typically, SSH is either installed by default or readily available in the package manager. Connect to the device locally (e.g., via a monitor and keyboard or an SSH client if already accessible) and use the following commands:
sudo apt-get update(Update the package list)sudo apt-get install openssh-server(Install the SSH server)sudo systemctl start ssh(Start the SSH service)sudo systemctl enable ssh(Enable SSH to start automatically on boot)
- Other Embedded Devices: Consult the device's documentation for instructions on enabling SSH. This may involve installing a specific SSH client or server package through the device's configuration interface.
After enabling SSH, make sure to take note of the device's local IP address. This can usually be found through the device's network settings or by using a network scanning tool on your local network.
2. Finding Your Device's IP Address:
To connect to your device remotely, you need to know its IP address. There are a few ways to find it:
- Local Network: If you have physical access to the device, you can often find the IP address displayed on its screen or configuration interface.
- Router's Device List: Most routers have a list of connected devices, including their IP addresses. Access your router's configuration page (usually by typing its IP address into a web browser, such as 192.168.1.1 or 192.168.0.1; refer to your router's manual for the correct address) and look for the list of connected devices.
- Network Scanning Tools: Use a network scanning tool (e.g., Nmap, Angry IP Scanner) on your computer to scan your local network and identify the IP address of your IoT device.
3. Configuring Port Forwarding:
Port forwarding is the critical step that allows external connections to reach your IoT device behind your router. The process involves configuring your router to "forward" incoming traffic on a specific port (usually port 22 for SSH) to the internal IP address of your IoT device.
- Access Your Router's Configuration Page: Log in to your router's web interface (see step 2).
- Find the Port Forwarding Settings: The location of these settings varies depending on your router's make and model. Look for sections labeled "Port Forwarding," "Virtual Servers," or similar.
- Create a New Rule:
- Service/Application: SSH (or a custom name)
- External Port: 22 (or a different port if you prefer to use a non-standard port for added security)
- Internal Port: 22
- Internal IP Address: The local IP address of your IoT device.
- Protocol: TCP
- Save the Rule: Save your port forwarding settings. Your router may require a reboot for the changes to take effect.
4. Using Dynamic DNS (DDNS):
If your internet service provider assigns a dynamic IP address to your router (meaning the IP address changes periodically), using a Dynamic DNS (DDNS) service is essential. A DDNS service provides a hostname (e.g., myiotdevice.ddns.net) that always points to your router's current IP address, even if it changes.
- Choose a DDNS Provider: Several DDNS providers are available (e.g., DynDNS, No-IP, DuckDNS). Select a provider and create an account.
- Configure DDNS on Your Router: Most routers have built-in support for DDNS. Enter your DDNS provider's credentials (username, password, and hostname) in your router's configuration page. The router will automatically update your hostname with your current IP address. If your router doesn't support DDNS directly, you can install a DDNS client on your IoT device or a computer on your local network.
5. Setting Up SSH Key Authentication:
Password-based authentication is a basic security measure and can be vulnerable to brute-force attacks. SSH key authentication is a much more secure alternative. It involves generating a public/private key pair and adding the public key to your IoT device. When you connect, you'll use your private key, and the device verifies your identity.
- Generate an SSH Key Pair on Your Computer:
- Open a terminal or command prompt.
- Run the command:
ssh-keygen -t rsa -b 4096 - Follow the prompts (you can usually accept the defaults). This generates two files:
id_rsa(private key, keep it secure) andid_rsa.pub(public key, you'll upload this to your device).
- Copy the Public Key to Your IoT Device:
- Use the command:
ssh-copy-id user@your_device_ip_or_hostname(replace "user" with your username on the IoT device and "your_device_ip_or_hostname" with the IP address or DDNS hostname). You may be prompted for your password. - Alternatively, manually copy the contents of your
id_rsa.pubfile and paste it into the~/.ssh/authorized_keysfile on your IoT device.
- Use the command:
- Test the SSH Key Authentication: Try connecting to your device using the command:
ssh user@your_device_ip_or_hostname. You should be able to connect without being prompted for a password. - Disable Password Authentication: To further enhance security, disable password authentication in the SSH configuration file on your IoT device (
/etc/ssh/sshd_config). Find the line:PasswordAuthentication yesand change it toPasswordAuthentication no. Restart the SSH service (sudo systemctl restart ssh) for the changes to take effect.
6. Adding VPN Protection (Recommended):
For the highest level of security, consider using a virtual private network (VPN). A VPN creates an encrypted tunnel between your computer and your home network. All traffic, including SSH connections, is encrypted, protecting it from eavesdropping and man-in-the-middle attacks, especially when using public Wi-Fi networks.
- Choose a VPN Provider: Several VPN providers offer services suitable for remote access (e.g., OpenVPN, WireGuard).
- Configure Your VPN: Follow the provider's instructions to set up a VPN server on your home network (this often involves configuring a server on your router or a dedicated device).
- Connect to the VPN: Install the VPN client software on your computer and connect to your home network's VPN server.
- Connect to Your IoT Device: Once connected to the VPN, you can SSH into your IoT device using its local IP address (on your home network).
By using a VPN, your SSH connection becomes much more secure, because all traffic is encapsulated inside a secure encrypted tunnel.
Advanced Considerations and Troubleshooting
Once you have established remote SSH access, there are some additional considerations and troubleshooting tips to optimize your setup:
- Firewall Configuration: Ensure that your router's firewall is configured correctly. If you're using a software firewall on your IoT device, allow incoming SSH connections.
- Security Best Practices: Regularly update the software on your IoT devices and router. Use strong passwords or passphrases and keep your SSH keys secure. Monitor your device logs for suspicious activity.
- Testing Your Connection: After making any configuration changes, test your SSH connection to ensure that everything is working as expected.
- Troubleshooting Common Issues:
- Connection Refused: Check that SSH is enabled on the IoT device, the device is online, and port forwarding is correctly configured on your router.
- Authentication Errors: Verify the username, password, or SSH key authentication.
- Network Connectivity Issues: Ensure that your router has a stable internet connection.
- Alternative Ports: You can configure SSH to listen on a non-standard port (other than port 22). This can help to reduce the risk of automated attacks, but it does not eliminate the need for strong security practices. When you use a non-standard port, you will also need to change your SSH client command to connect to that port, like this:
ssh -p 2222 user@your_device_ip_or_hostname, replacing "2222" with your custom port number.
Practical Applications and Real-World Examples
The ability to remotely access IoT devices opens up a range of possibilities across various domains:
- Smart Home Automation: Remotely control and monitor your smart home devices, such as lights, thermostats, security systems, and appliances.
- Industrial Automation: Manage and troubleshoot industrial equipment, sensors, and machinery from a centralized location.
- Remote Monitoring Systems: Access data from environmental sensors, weather stations, and other remote monitoring systems.
- Remote Server Management: Manage and maintain servers and other network devices located in remote data centers or offices.
- Educational Projects: Access and experiment with embedded systems, robots, and other educational platforms from anywhere.
For example, imagine a scenario where you have a Raspberry Pi running a home weather station with sensors. Through remote SSH access, you could:
- Retrieve Sensor Data: Download temperature, humidity, and pressure readings.
- Configure Alerts: Set up email notifications when certain environmental conditions are detected.
- Update Software: Install the latest software updates for your weather station.
- Troubleshoot Problems: Diagnose and resolve any issues with the sensors or the Raspberry Pi's software.
The Future of IoT Remote Access
As the Internet of Things continues to evolve, we can expect to see even more sophisticated and user-friendly remote access solutions. These might include:
- Improved Security Protocols: Advanced encryption techniques and authentication methods to protect against evolving cyber threats.
- AI-Powered Automation: Machine learning algorithms that automatically detect and respond to anomalies or security threats.
- Simplified Configuration Tools: Easier-to-use interfaces and automated setup processes, making it simpler for non-experts to configure remote access.
- Integration with Cloud Services: Seamless integration with cloud platforms for data storage, analysis, and device management.
The journey of secure remote access will continue to advance, but the fundamental principles discussed in this guide will remain central to safeguarding your IoT devices. By understanding these concepts and implementing the appropriate security measures, you can enjoy the full benefits of the Internet of Things while maintaining control and peace of mind.
Mastering remote SSH access for your IoT devices equips you with the skills to securely manage and monitor your devices from anywhere in the world. Following the steps outlined in this guide, you can protect your devices from unauthorized access and ensure the integrity of your network. As you embrace this technology, remember to prioritize security and regularly review your configurations to adapt to the ever-changing landscape of cyber threats. By doing so, you will empower yourself to unlock the full potential of the Internet of Things and experience its many benefits.
The combination of Secure Shell (SSH), port forwarding, Dynamic DNS (DDNS), and (optional, but recommended) VPN protection forms the foundation for securing access to your devices. By embracing these measures, you can manage your IoT devices securely, no matter where you are located.


Detail Author:
- Name : Fidel Dare IV
- Username : jennie.greenholt
- Email : lessie.mayert@yahoo.com
- Birthdate : 1988-03-04
- Address : 938 Novella Green Apt. 204 Wilfredhaven, AR 85458
- Phone : +1.757.617.1358
- Company : Feest-Champlin
- Job : Mapping Technician
- Bio : Magnam vel illum et quia. Hic optio ex odio molestiae labore atque.
Socials
facebook:
- url : https://facebook.com/summerkoch
- username : summerkoch
- bio : Quis repellat impedit vero dolorem velit voluptate sapiente.
- followers : 1849
- following : 2417
tiktok:
- url : https://tiktok.com/@skoch
- username : skoch
- bio : Corporis voluptatem nemo magni nostrum illum amet.
- followers : 704
- following : 2484
instagram:
- url : https://instagram.com/skoch
- username : skoch
- bio : Est quisquam non exercitationem aut ad. Recusandae sit repellendus sit. Harum harum voluptas iste.
- followers : 2480
- following : 2656
twitter:
- url : https://twitter.com/summer5203
- username : summer5203
- bio : Esse blanditiis quisquam autem labore eos sit nemo sequi. Dolore ut dolorum aliquam.
- followers : 2024
- following : 630